Table of Content
Access accreditation data on early learning and higher education program characteristics and quality for research purposes. We also provide many author benefits, such as free PDFs, a liberal copyright policy, special discounts on Elsevier publications and much more. This report provides an overview of the Acquisition Security Framework , a description of the practices developed thus far, and a plan for completing the ASF body of work. Libjpeg-turbo is a JPEG image codec that uses SIMD instructions to accelerate baseline JPEG compression and decompression on x86, x86-64, ARM, and PowerPC systems. On such systems, libjpeg-turbo is generally 2-6x as fast as libjpeg, all else being equal. On other types of systems, libjpeg-turbo can still outperform libjpeg by a significant amount, by virtue of its highly-optimized Huffman coding routines.

Changing operational and production priorities can often result in risk management falling to the backburner. When your team focuses on productivity and immediate deadlines, it is common for people to relax safety practices. It is important to place risk management as a core value of the company, ensuring that it maintains a high priority as things change in the work environment. Keep in mind that there isn’t a one-size-fits-all solution for determining the level of risk and priorities for your business. Through the risk assessment process, you need to identify the technique that works best for your unique situation.
Learn About Energy
It's useful for using a gamepad on PC games that do not have any form of built-in gamepad support. This program can also be used to control any desktop application with a gamepad. On Linux, this means that your system has to be running an X environment in order to run this program. This program currently works with various Linux distributions, Windows , and FreeBSD, but with limited support for FreeBSD and Windows XP. The Check Employment Status for Tax tool gives you HMRC’s view of a worker’s employment status, based on the information you provide.
SSO is an authentication process that allows you to access multiple services and applications with one username and password. Monthly senior management reviewBelow are presented scales for rating likelihood and consequence that can be applied to initiative risk and to system risk. The Heart Truth Healthy Hearts Network is a network of organizations around the country committed to promoting and raising awareness about heart health.
The Bunker: A Warning, a Weapon, a Windfall
Risk could also result in an otherwise undesirable outcome, with examples including bodily harm, legal or regulatory liability, or loss of property or productivity. A wider review of how people and businesses can better prepare for civil emergencies, involving consultation with risk communication experts is underway. The January 2012 version therefore does not include guidance on how to prepare for emergencies.
Tier 2 practices and systems support students who are at risk for developing more serious problem behaviors before those behaviors start. These supports help students develop the skills they need to benefit from core programs at the school. – an impact-based warning designed to highlight the potential impacts of extreme heat to protect lives and property, helping people make better decisions to stay safe and thrive. Some weather situations will bring impacts from more than one type of weather.
Related Events
Administration can implement procedures or systems that keep personnel working at optimal levels. Additionally, job rotation is another strategy that can reduce potential injury. Housekeeping, ergonomics, and hygiene all fall within the category of administrative controls. A risk assessment tool can be used to simplify the application of a risk matrix. For example, consider using an online form or mobile app, such as Safesite.
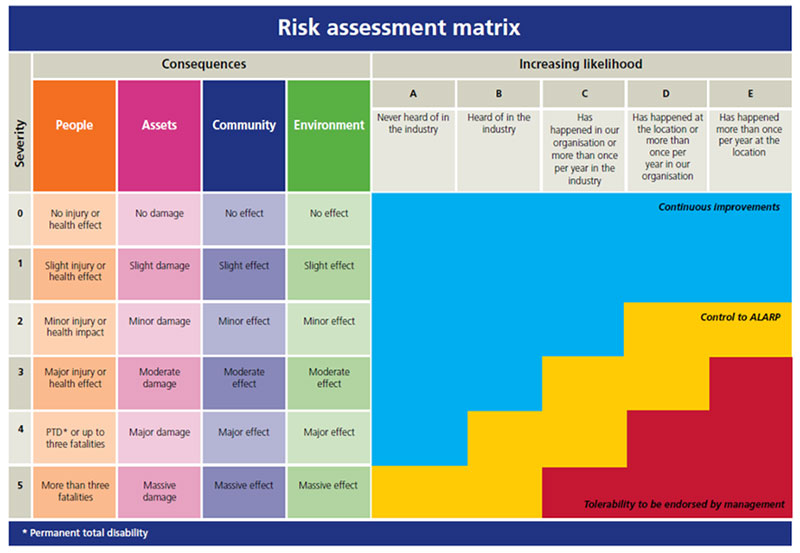
The following rating scale considers the resultant impact on the business should a risk occur and can be used in the assessment of consequence for ICT initiatives. The following rating scale considers the likelihood that a specific risk will occur and can be used in the assessment of likelihood for both ICT initiatives and ICT systems. The risk matrix diagram below follows the guidelines set out by Queensland Treasury and Trade A Guide to Risk Management—July 2011.
Table of Contents
Accidents and incidents should not happen in general, which is why every report should have a goal of preventing these incidents from happening again in the future. If it is found that this is not happening, then it would be a relevant aspect that needs to be included in the risk assessment. Historical workplace information can shed light on common, repetitive risk issues. Documentation needs to be kept about accidents and incidents, and this information can provide valuable insights to identify weak points in the system. While the reports can be helpful, it is also beneficial to talk to the people involved in the incident. Erick Brent Francisco is a content writer and researcher for SafetyCulture since 2018.
OSHA regulations vary depending on whether your business is in construction or general industry. The Department of Transportation has safety assessment regulations that change depending on the route of travel . The Environmental Protection Agency implements regulations to govern activities that impact the environment. Equipment malfunctions or breakdowns interrupts productivity and can result in potential danger to the safety of workers. Risk assessment is important for all equipment, but more essential in a workplace using older equipment. Some companies offer both of these types of services, which means that different risk assessments need to be used for various in-house departments.
Learn how you can live a heart-healthy lifestyle with the help of those closest to you. Epic eventually called on Microsoft to help argue its case in court, and Microsoft cranked up the pressure on Apple with some significant Windows store changes days ahead of the Epic v. Apple trial last year. Forms EIA uses to collect energy data including descriptions, links to survey instructions, and additional information. State energy information, including overviews, rankings, data, and analyses. Evaluation Brief This brief summarizes empirical research on the effects of Tier 1 PBIS for students with disabilities. When a warning is in force, it will be highlighted in the warnings banner on the homepage.
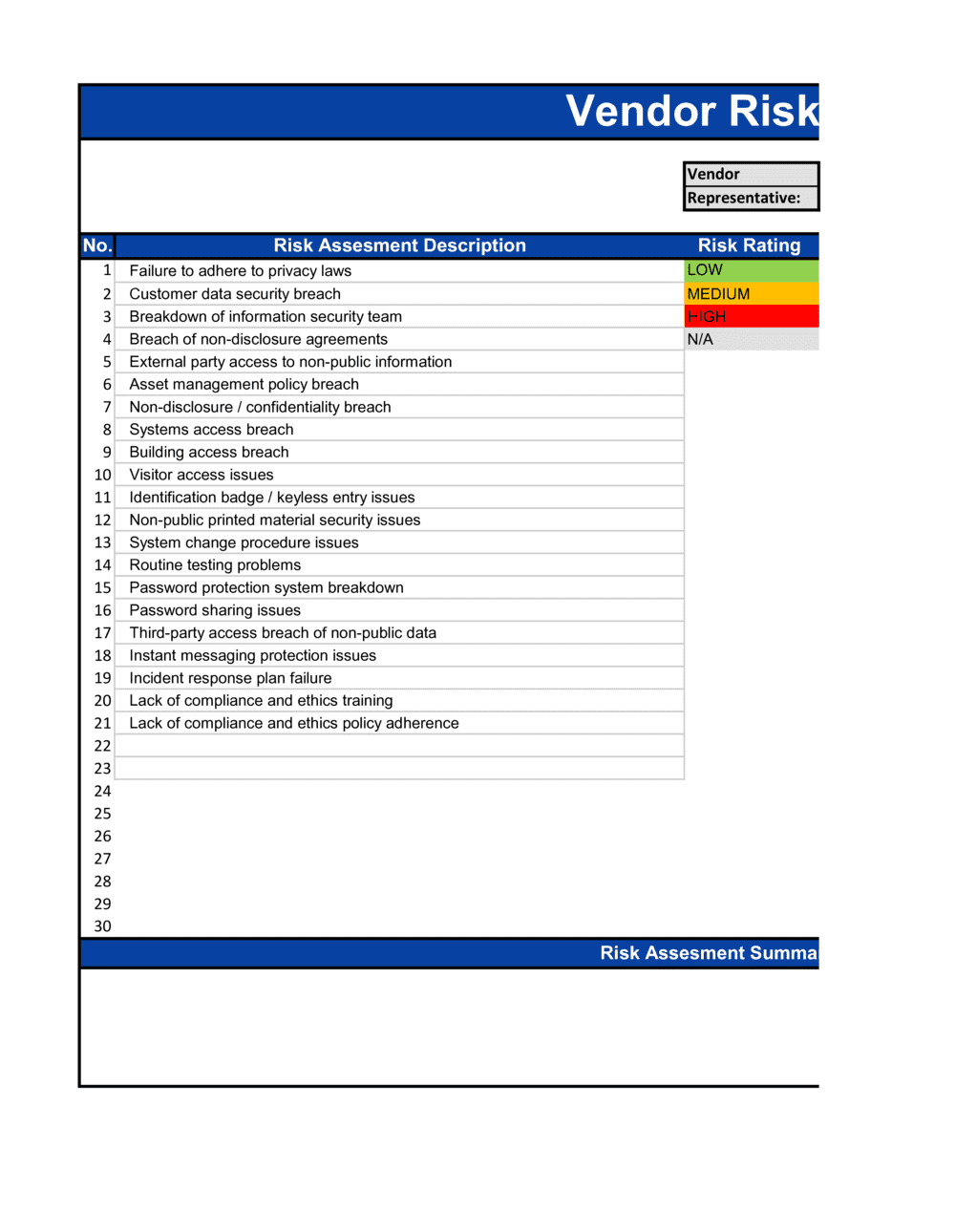
To get started, download for free any of our featured workplace risk assessment templates. Finding possible risks that, if they materialized, would have a negative impact on the organization's ability to conduct business is the first stage in a risk assessment. Natural catastrophes, cyberattacks, utility outages, and power outages are examples of potential risks that might be taken into account or discovered during the risk assessment process. In many projects, risks are identified and analyzed in a random, brainstorming, fashion. It is essential that potential risks are identified, categorized, evaluated & documented.
Now you can automatically implement patches and upgrades across your entire network in minutes. 30 March 2017 Added a link to the off-payroll working in the public sector guidance. When this happens, the tool will give you further information to help you reach your decision. You do not need to know who the worker is to use the tool – you’ll still get a result.


No comments:
Post a Comment